Welcome back, my tenderfoot hackers! Do you need to get a Wi-Fi password but don't have the time to?
In previous tutorials, I have shown how to crack,, and, but some people have complained that cracking WPA2 takes too long and that not all access points have WPS enabled (even though quite a few do). To help out in these situations, I present to you an almost surefire way to get a Wi-Fi password without cracking—.
Steps in the Wifiphisher Strategy The idea here is to create an, then de-authenticate or DoS the user from their real AP. When they re-authenticate to your fake AP with the same SSID, they will see a legitimate-looking webpage that requests their password because of a 'firmware upgrade.' When they provide their password, you capture it and then allow them to use the evil twin as their AP, so they don't suspect a thing. To sum up, Wifiphisher takes the following steps: • De-authenticate the user from their legitimate AP. • Allow the user to authenticate to your.
I have a late 2012 MacBook Pro running OS X 10.9 Mavericks, and it uses a network login system with my school. This normally wouldn't be a problem, except for the fact that I can't connect to a wifi network from the login screen.
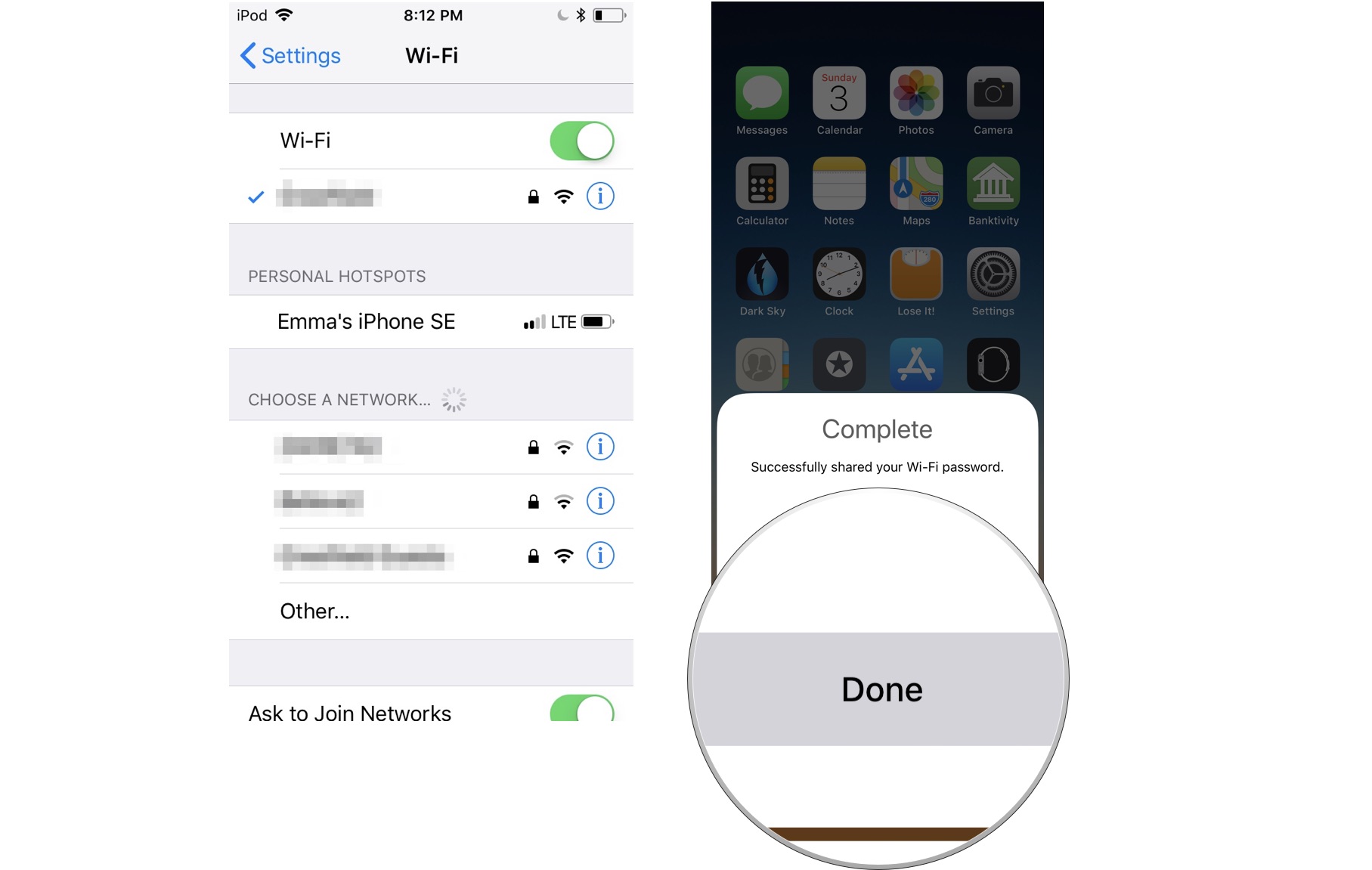
Your statement that Therefore, this must be an issue with my device- a MacBook air- and not with the router. Is not necessarily the case here. One thing to try is to switch off your router for at least a minute and then reboot it.  After reboot, test again with both your MBA. I have my cable modem into a router, then 4 more routers in my house connected through, cables, switches, etc to get more WIFI in my huge, old, thick walled house.
After reboot, test again with both your MBA. I have my cable modem into a router, then 4 more routers in my house connected through, cables, switches, etc to get more WIFI in my huge, old, thick walled house.
Microsoft Windows implements multiple user accounts with functionality similar to Mac OS 9. UNIX, on the other hand, was designed to be a multiuser environment because most computers in existence at the time UNIX was developed were large computers that had to be shared by many users. If you have multiple networks of different names your Mac or iPhone will always choose the first in your iCloud-synced 'Preferred Networks' list even if this one isn't going to give you the best.
Ipads Have Different Wifi Speeds
• Offer a webpage to the user on a proxy that notifies them that a 'firmware upgrade' has taken place, and that they need to authenticate again. • The Wi-Fi password is passed to the hacker and the user continues to the web oblivious to what just happened. Similar scripts have been around for awhile, such as, but this new Wifiphisher script is more sophisticated. In addition, you could always do this all manually, but now we have a script that automates the entire process. Recently, another script named Fluxion has also gained popularity as an alternative to Wifiphisher. You can if Wifiphisher isn't working for you.
To do this hack, you will need and two network wireless adapters, one of which must be capable of packet injection. You can use the tried and true, or check out our guide on for Kali Linux. Don't miss: You may use others, but before you do, make certain that it is compatible with (packet injection capable). Please do NOT post questions on why it doesn't work until you check if your wireless adapter can do packet injection. In your previous tutorial on evil twin a fake AP wwas created with the same BSSID and ESSID as the ap to be hacked and you could only see one AP because the fake one overwhelms the orginal. But in this tutorial the scritp or tool creates an AP with only the same ESSID as the original hence you see actually two APs one open and secured so it's suspicious and devices won't connect automatically so the user would actually have to choose to connect to the fake one don't you think it's better to edit the python script to have the fake AP have the same BSSID as the original like in your previous evil twin tutorial?? Being online should not be mandatory.
After you got the password you can simply stop the fake AP, victim will disconnect and reconnect to real one automatically. Or you could automate it by adding a small script to stop the attack as soon as the victim inputs the password. Password validation can be added as well, either trying to authenticate with the just gotten password, or using aircrack against a previously captured wpa handshake. Again, this can all be scripted and executed when victim types his password.
This way attacker might know in real time if password is correct, and eventually output the result in the phishing page before stopping the attack. So in case a suspecting user types some gibberish in the password field, it won't be greeted with 'YAYYY Password is correct'!! Personally, I don't always type my passwords when they try to phish me, but when I do, I type some gibberish password that ends with ' OR 1=1 Reply. In the firmware upgrade page, is there an option to notify the user in the first attempt that the credentials provided were wrong so that people who hesitate to put usernames and passwords in suspicious looking pages could be tricked. Doing this on the first login attempt could fool the people who might insert wrong credentials intentionally in the first attempt to see how page responds.